
Over the past decade, there has been a dramatic change in the best practice password standards pushed by leading organisations. Are companies and their auditors being too slow to understand and implement these changes to control frameworks?
Historically, password rotation alongside increased complexity requirements have bern the drivers for system security. Organisations such as NIST (National Institute of Standards and Technology) in the US, and NCSC (National Cyber Security Centre) in the UK, both recommended standardised password requirements applicable to all accounts. Routine password rotation of between 30 and 90 days was common.
Increases in computing power meant that passwords were becoming far easier to crack, especially against known common passwords and passwords that were not complex in nature.
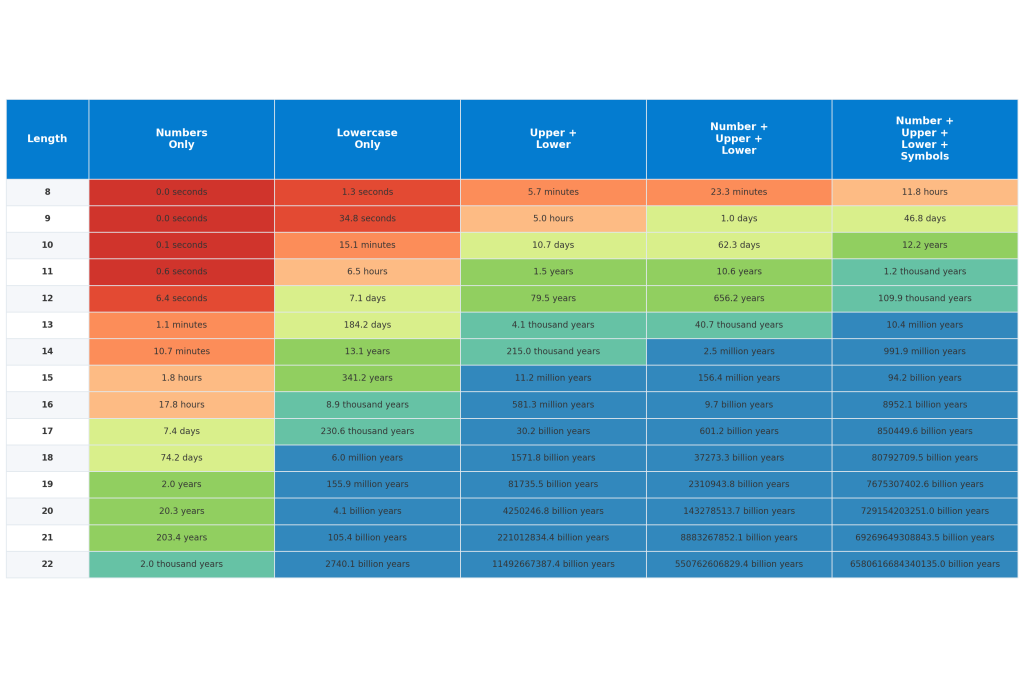
If we proceed forward to current standards, almost all of these guidelines have moved away from time-based password expiry, moving towards risk-based password changes e.g. in the event of a known breach or password leak. There are a number of reasons for this, primarily that enforcing password rotations often leads to weaker password combinations that are iterations of previously used passwords. Additionally, there have been pushes towards other elements such as increased password length and use of multi-factor authentication. These make passwords harder to crack and requires an additional physical key (‘something you have’ or ‘something you are’, or sometimes both) to accompany the ‘something you know’.
Following this discussion, it might seem straight forward. However typically this still causes an issue when being audited, even if following the latest standards. The standards often quoted relate to end user accounts belonging to a single person. Often an area which causes issues are in relation to generic accounts, which can be accessed by multiple team members. Typically, due to the risk of the password being known to an individual who subsequently doesn’t require access, however unlike an end user account where the access can be modified or disabled the generic account retains this access, auditors expect additional requirements for these accounts. As standard, rotating these passwords yearly meets the criteria’s auditors follow including SOX 404.
Password standards feel like these should be simple and easy to comply with, however given contradicting authentication standards and differing auditor expectations – this simple topic can be anything but.